In a time when knowledge travels easily across national boundaries, the digital sphere is becoming a more important arena for power struggles. The Microsoft Threat Analysis Center (MTAC) has released a paper that highlights the sophisticated cyber operations and influence efforts that are being conducted by East Asian entities, with a particular focus on North Korea and China. These state-sponsored initiatives seek to influence public opinion globally in addition to endangering the cybersecurity environment. This lengthy piece explores the specifics of these operations, their ramifications, and the cooperative attempts to lessen their effects.
Chinese Influence Operations: A Multi-Pronged Strategy
Social Media Deception and AI-Generated Content
China uses a variety of strategies for its influence operations, including the use of AI-generated material and fictitious social media profiles to sway public opinion. In order to gather intelligence and deepen social tensions, CCP-affiliated players assume the identities of common American voters and engage in divisive debates on domestic matters. Precious election seasons have been distinguished by a considerable rise in activity on these accounts, which suggests a calculated attempt to sway the political process.
Inauthentic Chinese social media accounts try to learn more on what divides US voters
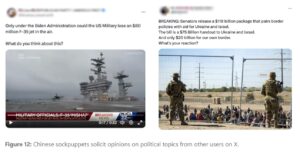
Furthermore, China’s deliberate aim to increase its influence is shown by its use of AI-generated information to sway opinions about world events. These operations use current events, such as the Maui wildfires and the Japanese nuclear wastewater disposal, to paint the United States and its allies in a bad light. Evidence shows that these initiatives, despite their wide reach, have not yet had a substantial impact on public opinion or election results.

Unwavering Geopolitical Goals
The study emphasizes China’s steadfast geopolitical goals, concentrating on key areas including the South China Sea and the South Pacific islands. China’s influence efforts have become more sophisticated, demonstrating a strong commitment to furthering its objectives internationally. Particularly, the actions of the organization Storm-1376 show a deliberate attempt to use AI-generated misinformation operations to influence events such as the Taiwanese presidential election.
North Korea’s Cyber Endeavors: Funding Through Felony
The Cryptocurrency Heist Strategy
Financial motivations drive North Korea’s cyber activities, which include supply chain hacks and cryptocurrency heists intended to transfer funds to the nation’s armed forces and intelligence services. The regime’s need on cybercrime to sustain its sanctioned economy is highlighted by these cyberrobberies, which are believed to have brought in over $3 billion since 2017.
Leveraging AI for Enhanced Efficiency
There is a trend towards more complex methods as there are emerging allegations of North Korea using AI technologies in its cyber operations. One example of how Microsoft and OpenAI are working together to counter the North Korean outfit Emerald Sleet is how persistent attempts are being made to defeat these sophisticated attacks. North Korea is an increasing threat to international cybersecurity defenses as it seeks to improve the efficacy and efficiency of its cyberattacks by utilizing AI technology.
Collaborative Countermeasures and the Path Forward
Microsoft and OpenAI’s collaboration is a critical development in the battle against state-sponsored cyberthreats. Public-private partnerships have the ability to improve cybersecurity as evidenced by the effective neutralization of accounts and assets associated with criminal operations through their combined efforts.
The MTAC analysis predicts that China will keep developing its use of AI-generated information to sway international affairs. While the effect of these campaigns on election results is now negligible, the dynamic nature of these strategies may provide a big obstacle in the road. It is also anticipated that North Korea would continue to concentrate on cyber espionage and cryptocurrency theft, highlighting the need of global collaboration and innovation in cybersecurity tactics.
The advent of the digital era has presented previously unheard-of difficulties for information warfare and cybersecurity. The MTAC report’s extensive account of China’s and North Korea’s efforts highlights the intricate and ever-changing challenges that governments throughout the globe face. As cyber operations get increasingly complex and influence efforts more subtle, the international community has to be cautious and watchful. To protect democracy and provide a safe online environment for everyone, cooperation, technical innovation, and a dedication to digital integrity are crucial.


