The U.S. Department of Justice has launched a major nationwide crackdown on a large-scale North Korean scam targeting American companies. This powerful action, announced on July 1, comes after a long investigation into how North Korean workers secretly got jobs with U.S. companies using fake names and stolen identities.
Over 100 American companies, including Fortune 500 businesses, were tricked into hiring these workers. The jobs were mostly for remote IT (information technology) positions. But the people doing the work weren’t who they said they were. They were North Koreans pretending to be American citizens or people from other countries.
According to U.S. officials, these fake workers got access to private company information and even top-secret technology. Some of them stole virtual currency and other sensitive data. North Korean operatives secretly earned and sent money back to fund the government’s weapons programs.
Arrests, Indictments, and Seizures Across the Country
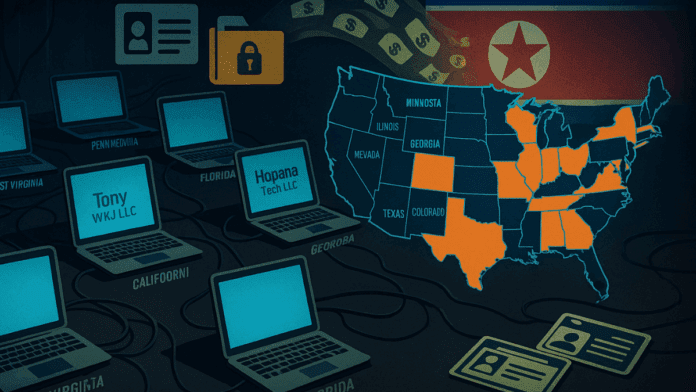
One of the main suspects arrested is Zhenxing “Danny” Wang, a U.S. citizen from New Jersey. Prosecutors accuse him of helping North Korean workers get jobs by creating fake companies like Hopana Tech LLC, Tony WKJ LLC, and Independent Lab LLC. These companies had fake websites and bank accounts to make the scam look real.
Wang is not the only one charged. The government has also filed charges against several other people, including:
- Kejia Wang, who worked closely with Zhenxing Wang and traveled to China to meet with overseas co-conspirators.
- Jing Bin Huang, Baoyu Zhou, Tong Yuze, Yongzhe Xu, Ziyou Yuan, and Zhenbang Zhou from China.
- Mengting Liu and Enchia Liu from Taiwan.
Officials say that this team helped set up laptop farms — places where computers were kept so North Korean workers could access them from overseas. These computers belonged to real American companies. The fake workers logged in from other countries, pretending they were in the U.S.
In total, the Justice Department searched 29 locations across 16 states, including 21 known or suspected laptop farms. They seized about 200 computers, 29 financial accounts, and 21 fake websites used in the scam.
HMS Spey Returns to War Zone Waters—13th Deployment to Halt North Korea’s Sanctions Evasion
North Korean Nationals Stole Over $900,000 in Cryptocurrency
In a separate case, four North Korean nationals — Kim Kwang Jin, Kang Tae Bok, Jong Pong Ju, and Chang Nam Il — have been indicted for stealing more than $900,000 in cryptocurrency from two companies. One of the companies is based in Atlanta, Georgia. The suspects used fake identities like “Bryan Cho” and “Peter Xiao” to get hired. Once they gained trust, they stole virtual currency and laundered the money using a cryptocurrency tool called Tornado Cash.
They used fake Malaysian identification documents to open accounts and hide their North Korean backgrounds. The perpetrators sent the stolen money to exchange accounts under false names and eventually transferred it to North Korea.
These North Korean actors are still at large and wanted by the FBI.
Between June 10 and June 17, 2025, the FBI carried out additional searches in 14 more states. They took 137 laptops and collected important evidence linking the laptop farms to this illegal scheme.
The investigation, known as DPRK RevGen: Domestic Enabler Initiative, is part of the U.S. government’s plan to stop North Korea from secretly making money through cybercrime. Officials say that some of these fake workers even accessed military-related information and sensitive source code from U.S. companies.